In this blogpost I am going to take you through the steps to setup an site to site VPN from your small office / Home office (SO-HO) using UniFi Ubiquiti equipment. My setup contains 2 Unifi AP AC PRO’s, an Unifi 8 port 60W POE switch, Unifi cloudkey and the Unifi Security Gateway. To setup an VPN to Azure the minimal Unifi equipment you need is the security gateway.
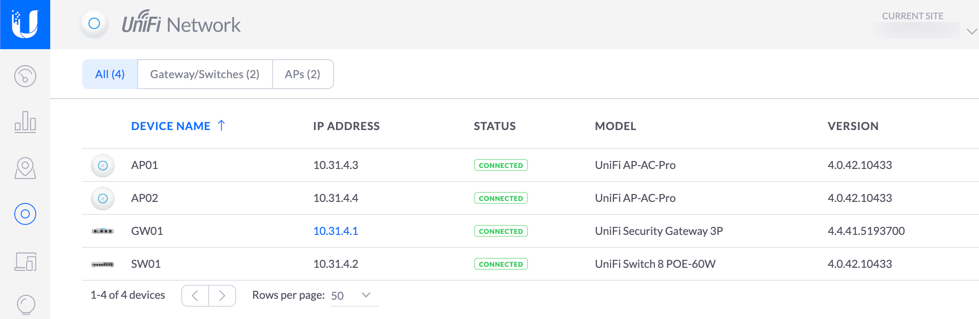
So I already have deployed in Azure and configured the following network resources:
- 1 Azure Virtual Network (VNET) with a Client subnet and an Azure GatewaySubnet
- Azure VPN Gateway (Gateway connected in my gateway subnet)
- Local Network Gateway (object that represents my Unifi SG)
- Connection resource (that establish the connection between the Azure VPN Gateway and Local Network Gateway)
- VM (Here I will connect to using internal ip to verify tunnel is up)
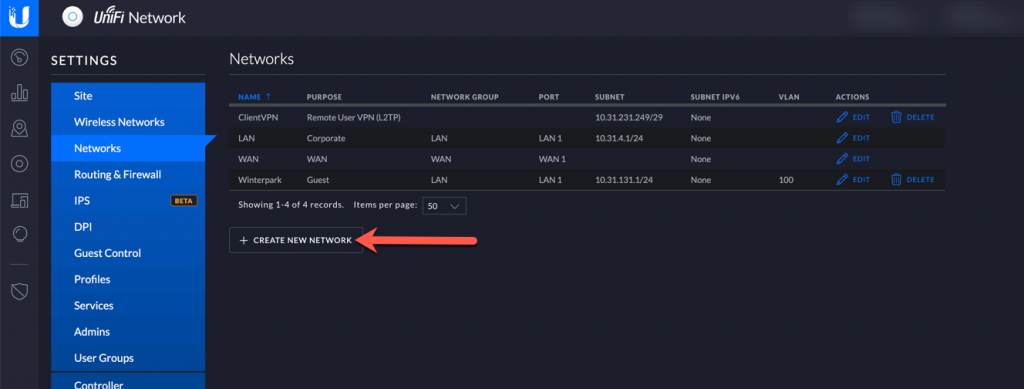
Connect to your Unifi environment using Cloudkey and enter the settings page. Next, select the networks section and choose to “Create new network”
In the new network section choose for Site-to-Site-VPN and give it a name that is easy to refer to for you. Select the Manual IpSec option and head over to the Add Subnets section and add the subnets that reside in the Azure Virtual Network. If you have vnetpeering with other vnets and want to be able to connect to those networks as well add these subnets here too.
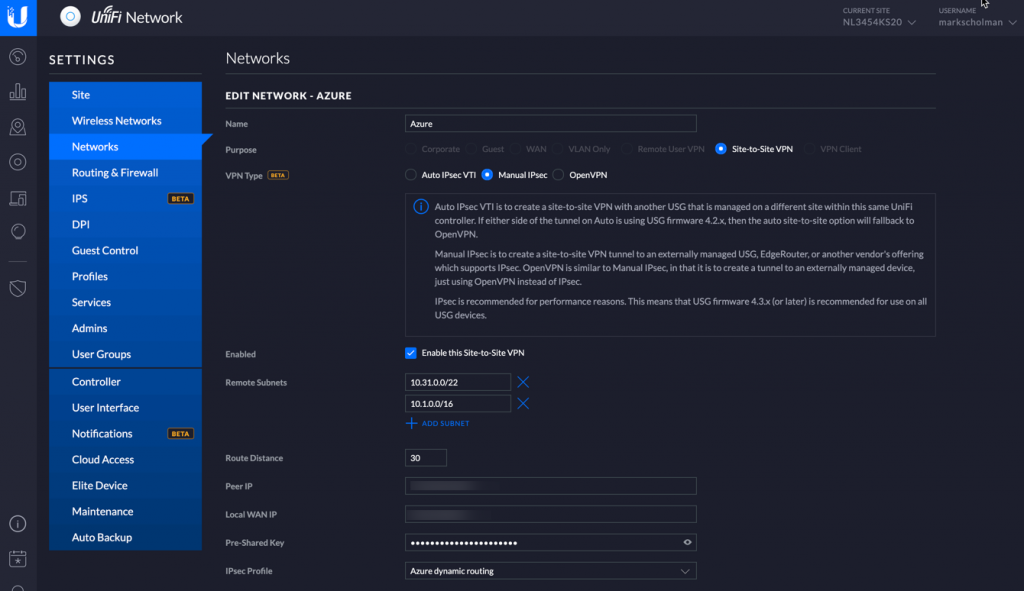
Leave the Route Distance to default value and enter the peer IP address, which is the IP address of the Azure Virtual Network Gateway and the local WAN IP, which is the external ip of your unifi router. Finally, enter the pre-shared key and set the IPSec profile to Azure Dynamic Routing. If you expand the advanced options section you will see IKEv2 is used for the VPN connection. Click save to submit the form and establish the VPN.
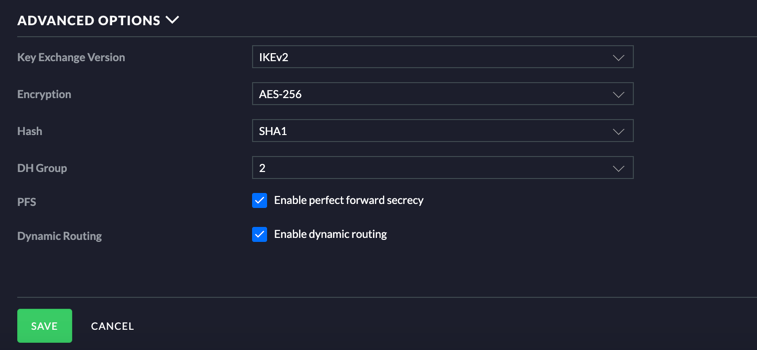
After a few minutes check the connection status and it should be Connected. This means traffic should be able to flow via the VPN between on premises and your Azure Network.
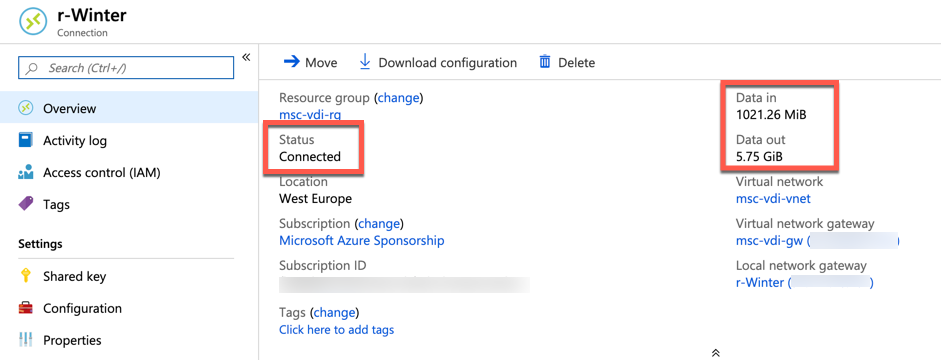
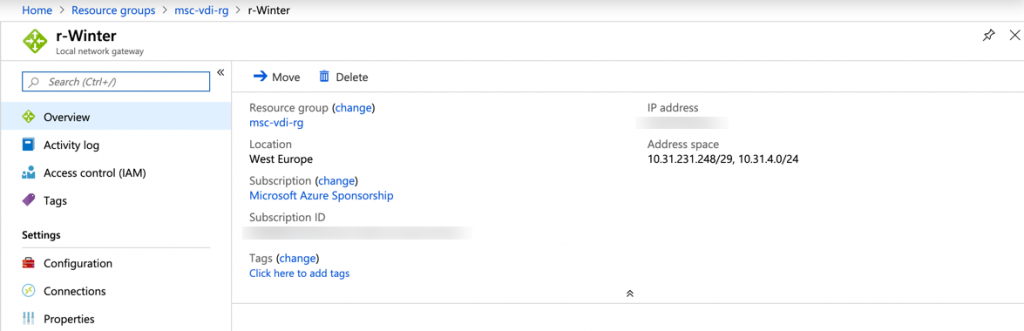
Common mistakes made are configuring the wrong pre-shared key on the connection resource and not including all subsets that are reachable on each end. These can be configured on the local network gateway side.
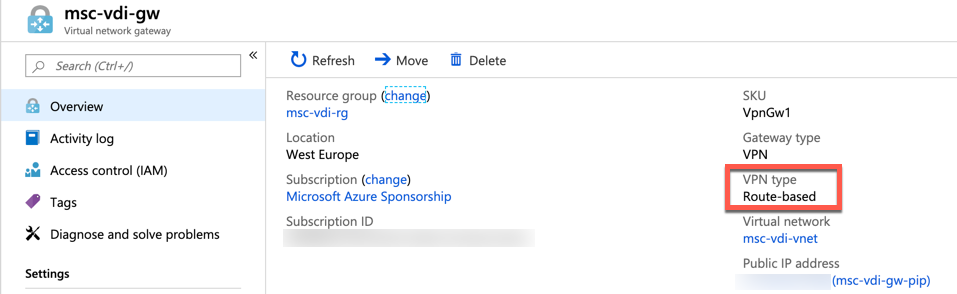
Also check that the gateway has been setup in route-based mode as shown here:
Happy networking!
