When you need to configure a test sip trunk or implementing a sip trunk in a Small business that is provided over the internet behind (NAT) a Cisco ASA firewall you might run into a REQUIRE: rel100 followed by a 408 timeout issue.
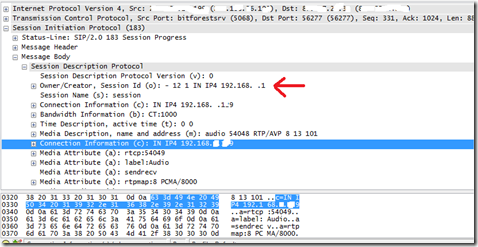
This is because the media path back from your sip trunk provider is sending back the media stream to the internal ip of your (collocated) mediation server.
As you see in the wireshark capture above believe me as I said the src and dst are external ip’s, But the SIP Message body is a private ip.
You need to configure your ASA to hide the internal IP from your mediation server so that the NAT public ip is seen by your SIP trunk provider. We used the following steps to achieve this:
We used in our configuration to configure the sip port to our provider at port 5060 and configured to listen our mediation server to listen on port 5068.
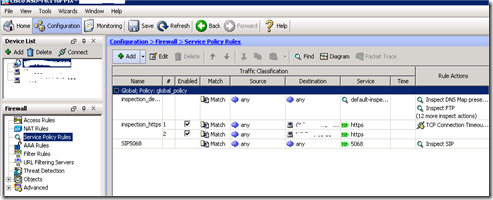
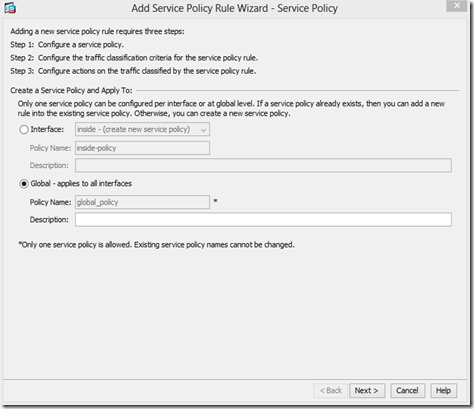
In the Firewall configuration go to Configuration –> Firewall –> Service Policy Rules:
Edit the default inspection rule by selecting it and click edit:
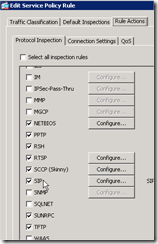
Then go to Rule Actions and under protocol inspection scroll down to SIP and click configure:
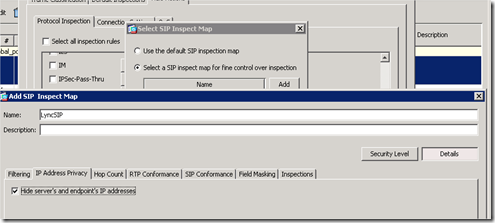
Select the box “ Select a SIP inspect map…” and choose add. Give your rule a name and select details. Then the second tab select the Hide server’s and endpoint’s IP addresses. Leave all other options default and click OK and OK. You can find the Inspect map back under the following menu:
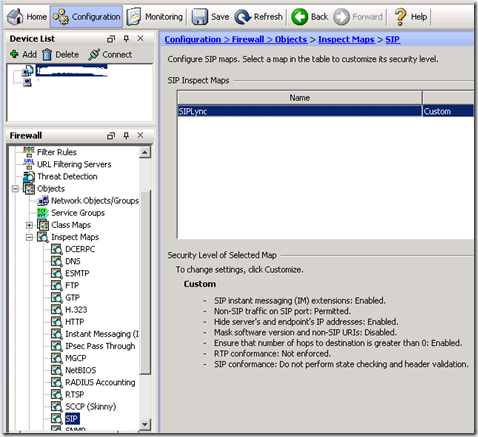
Configuration –> Firewall –> Objects –> Inspect Maps –> SIP
Next we need to create a new rule for the incoming port 5068. We need to go back to the Service Policy Rules and click Add, select Global and choose next:
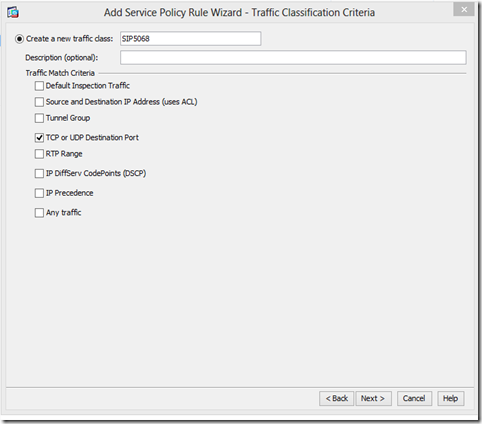
Then assign traffic class name and choose TCP or UDP destination port:
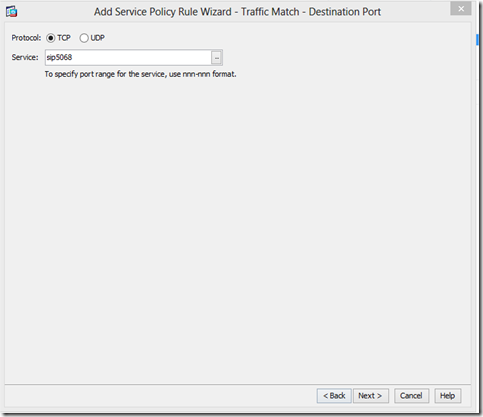
Use the port you specified for NAT translation to your mediation server. In our case we use tcp 5068
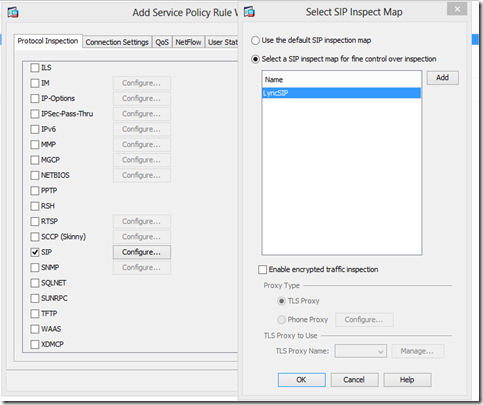
Select SIP and click on Configure, then select the inspect map we created earlier and click OK and Finish:
Verify the rule is added:
And that’s it! Now if all number routes are configured correctly and assigned to users the inbound calling is working.