In this post I am configuring a test case for Multi-Factor Authentication. We are going to convert a existing remote desktop gateway deployment with username / password authentication and a central NPS running on ADC to use the MFA.
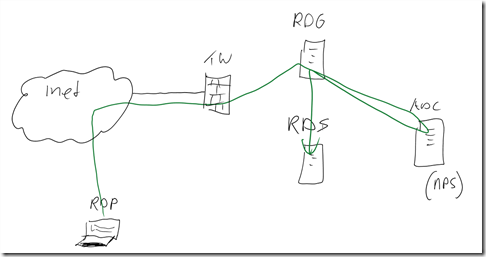
As I like to use oneNote with pen on my Surface more then I do Visio I have quickly put a diagram of the situation I have now:
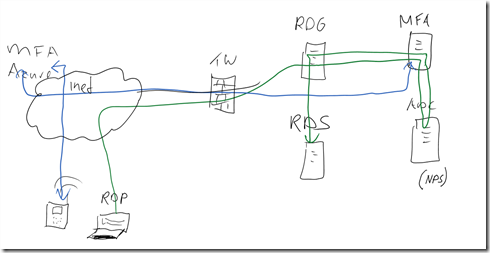
And below the situation what I have in mind for use of Multi Factor Authentication:
So here we go…
First I am going to configure the MFA to act as a proxy Radius in between the RDG and ADC (NPS in my situation).
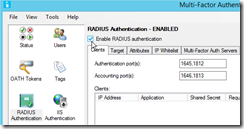
I am going to add the RDG as an Client for the MFA proxy
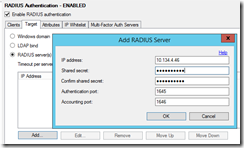
As Radius proxy I am going to send my request to the Radius Server (Target):
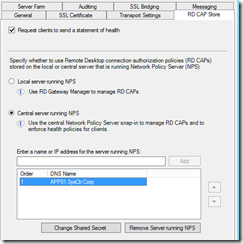
On the Remote Desktop Gateway I am removing the ADC Server as central policy server and add the MFA server (proxy radius):
After changing the setting open the NPS Console on the RDG server. We need to change the timeout settings for the request to the radius server as we need time to authenticate to the Azure MFA, answer the call or click the app and then send the authentication back to the radius.
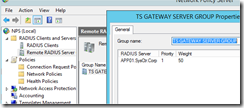
Under Remote Radius Server open the TS Gateway Server Group. Then choose edit.
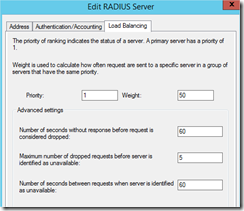
At the Load Balancing tab set the Number of seconds without response before request is considered dropped to 60 seconds.
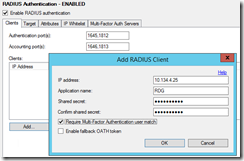
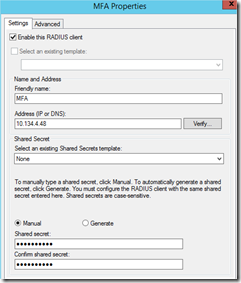
On the NPS server (my case the ADC) I need to add MFA server as radius client. So I open the NPS Console on the ADC and add new radius client :
Here I have created the MFA Radius client on the ADC:
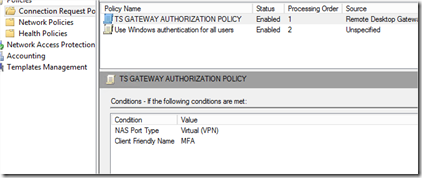
Now on the Connection Request Policies I added the just created Client Friendly name (MFA) as condition so only the MFA Proxy can authenticate to the NPS for connecting and authenticating the RDG requests:
If I have deployed and configure a user for the Remote Desktop gateway and MFA (phone number or App) I should be able to login the Remote Desktop servers. In my case I did ![]()
I hope these series gave you a quick understanding of how On Premise Multi-Factor Authentication works and how you can use it in your environment.